
If you haven't checked out my 3 Cybersecurity (paid) mini-courses at WintellectNow, now would be a great time. Designed with a non-expert in mind, these courses can help you get your bearings in hands-on matters of Cybersecurity, from managing private information to ensuring the personal data of your clients stays confidential. My WintellectNow profile below is a good place to start. Cheers!
https://www.wintellectnow.com/Home/Instructor?instructorId=zacharias-voulgaris
Altri post di Zacharias 🐝 Voulgaris
Vedere pubblicazioni
My latest (not-so-technical) article
Zacharias 🐝 Voulgaris · Lately, I haven't written much because of the intense workload. Nevertheless, this past weekend I carved out some time to put together a (not-so-technical) article, which I published on my blog. You can find it here. · I hope you find it interesting and perhaps thought-provoking. ...

Polywork
Zacharias 🐝 Voulgaris · Polywork is a relatively new platform that appeals to the emerging kind of professional who is more of a generalist or a versatilist. Its aim is not to brand people as specialists in this or the other field but rather provide a birds-eye view of their lives and the variety of ser ...

My latest mentoring article
Zacharias 🐝 Voulgaris · I put a lot of effort into this and made sure it can be a value-add, regardless of your role in a mentorship. · Mentoring Best Practices · Some ideas to help cultivate and refine a mentoring relationship in practice · https://aigents.co/data-science-blog/career-blog/mentoring-bes ...
Articoli di Zacharias 🐝 Voulgaris
Visualizza il blog
What Is Data Strategy Anyway? · Data strategy is a way to utilize data to produce insights useful fo ...

I've never had any serious issues with my digestive system, but it doesn't hurt to be prepared. Afte ...

Overview · Lately, many professionals in the data world offer mentor and consult services. Oftentime ...
Contenuto correlato

Zacharias 🐝 Voulgaris
Can We Have a Secure Enough Cybersecurity System in Our Daily Workflows?
Recently I came across a video on Minds about an upcoming crisis that’s been already talked about by all those do-gooders at the World Economic Forum (I’m being sarcastic here). So that they don't catch anyone by surprise, I'm sharing with you my insights on this topic, which I'v ...

Zacharias 🐝 Voulgaris
The Two Types of Two Factor Authentication and How They Impact Cybersecurity
Two Factor Authentication (2FA): a security system that requires two distinct forms of identification in order to access something. · Cybersecurity: the measures taken to keep electronic information private and safe from damage or theft. · (Security) Token: a portable device that ...
Zacharias 🐝 Voulgaris
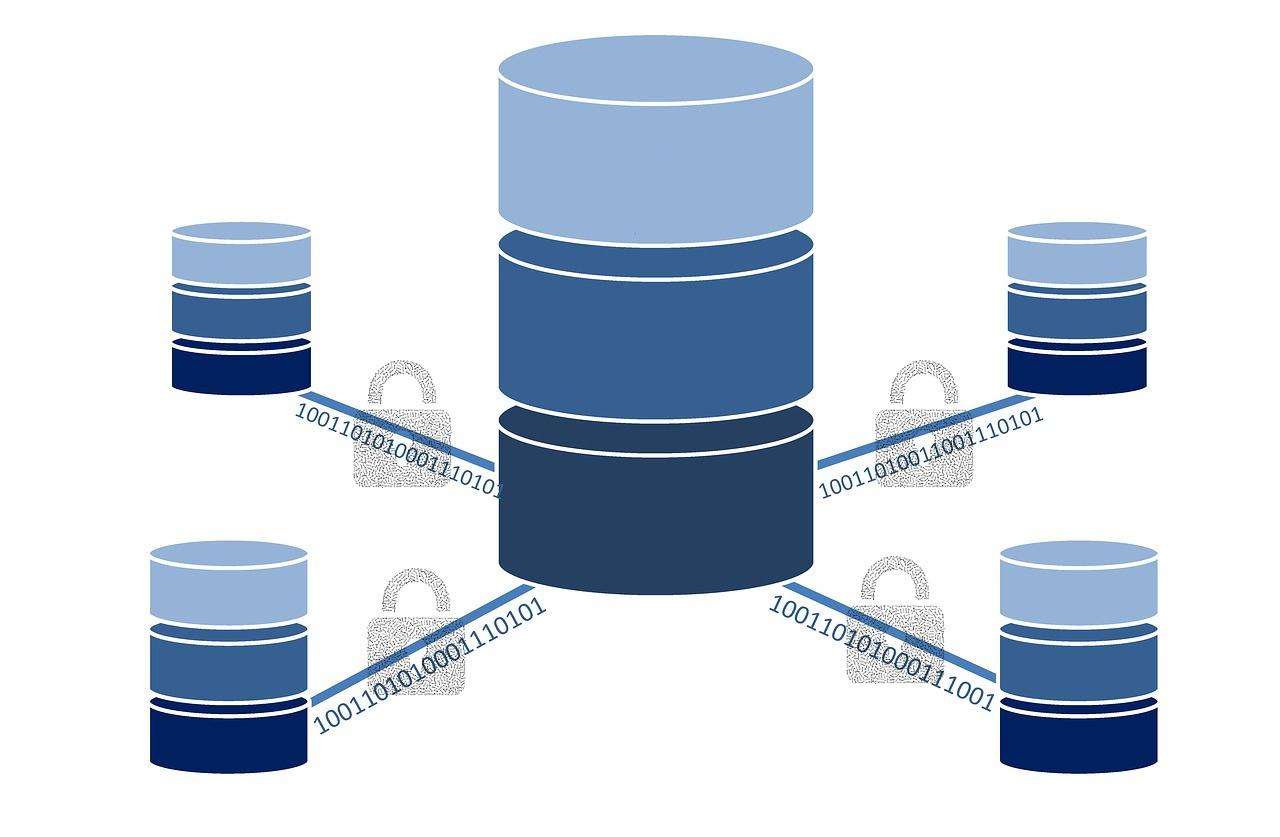
Data Management Best Practices for Modern Backend Data Security
Source: pixabay.com (after some processing work)The Backend Data Security Threat Is Real! · Unless you’ve been living under a rock, chances are that you’ve heard of at least one of the many data security breaches that have taken place in the past year. Also, if you’ve been paying ...

Zacharias 🐝 Voulgaris
Cybersecurity courses for non-experts
It's interesting how my 3 Cybersecurity (paid) mini-courses at WintellectNow are still highly relevant even a year after their publication. Designed with non-experts in mind, these courses can help you get your bearings in hands-on matters of Cybersecurity, from managing private ...
Professionisti correlati
Non hai gruppi che si adattano alla tua ricerca
Commenti